This article gets into the details how Bitcoin transactions work. For a less involved overview of Bitcoin, read our Introduction to Bitcoin post.
Understanding Bitcoin Transactions
Two things are needed for transactions.
- Trust between the people doing the transaction
- Verification of the transaction
Hmm, that sounds easy but let’s pull the curtain back. Let’s use a typical real estate sale such as a home purchase as an example.
Trust
Most real estate transactions require a contract to guarantee trust. The contract lays out the details of the seller’s property and the price the buyer is willing to pay for the property. The contract was prepared at some point by lawyers.
Verification
Lawyers or a title company do some amount of background work to ensure the property is the seller’s. They also insure the property is the seller’s as part of the title commitment. They also act as the intermediary to transfer the buyer’s money to the seller.
Trust and Verify With Computers
What if you could use computers to ensure the trust and verify the transaction? Satoshi Nakamoto’s white paper proposed a clever way to accomplish both goals with computers.
Establishing Trust Between Computers
In the Middle Ages, kings used a royal seal to prove a document came from them. A royal seal was simply an elaborate design that was pressed into melted wax that sealed the letter. In order to open the letter, the receiver had to break the wax seal. It was assumed that once broken, the seal couldn’t be put back together again.
The seal had 2 purposes as follows:
- 1. The seal’s elaborate design validated the letter had come from the king.
- 2. If the wax seal was intact, it was assumed that no one else had opened the letter.
In modern times, cryptographic keys are used as the royal seal and we don’t need to be kings or queens to have our own keys.
It is useful to think of keys as coming in pairs – a private key and a public key. The public key actually comes from the private key but they are not the same number. The neat part is that you can generate multiple public keys from a private key which is very useful for Bitcoin transactions as we’ll see below.
Another important characteristic is that creating a public key from a private key is a one-way function. In other words, you can’t get the private key back from the public key.
Explain One-Way Function Cryptography as ELI5?
Wikipedia describes a one-way function as easy to calculate if you know the input but hard to reverse-engineer if you don’t know the input.
Bitcoin has a lot of complex math but to show the idea, we’ll use a simpler example.
Let’s use remainders as an example. Let’s say our equation is: divide by 10 and use the remainder for the public key.
In this example, we’ll say our private key is 297. Now according to the equation we need to divide by 10 and use the remainder.
297 / 10 = 29 with a remainder of 7.
So our private key is 297 and our public key is 7.
Can we figure out the private key from the public key? Well, sorta but it could take many iterations to find.
If we know the equation and the public key, the private key could be 7, 17, 27, 37, 47, 57 … and so on up into the millions. You would need to check every one to see if it is the private key. You get the picture and this is a simple example. With large numbers it just isn’t worth it.
Another use of one-way cryptographic functions is with hash functions. Hash functions are used to represent a number with a smaller number. In the example above, 123456 could be represented by 6 as well.
Back to Private and Public Keys
Either key can decode a message that was encoded with the other key. Normally, a private key is used to encode the message and a public key is used to decode the message.
If Alice is sending Bob a message, she will send him the public key initially.
Then Alice will write a message.
Hi Bob. This is Alice and when you decode this message with the public key, you'll see it is me and can verify this message came from me. Alice
Then Alice will encrypt the message with her private key giving this:
-----BEGIN PGP MESSAGE----- Version: OpenPGP v2.0.8 Comment: https://sela.io/pgp/ wcBMA+t5mJvj0F3yAQf/Q5dzIE2W0mdDXxrN2HliM0BzlwpoSXO0Oqcuq9X5+u4U MY91vH58dKmGPRw35oGTRA+sEJcF2MNlB04vzgurd95rhg0iNh+36ndLqIDU6M9G bW9D4n7hAaijcr6gf3GTgKklW30mu1QjXvxNDFhAouiSuFH0vMme9zMcyS6Gfmfn DGNatUXNeEFwfbjIByJa2WQl6BgMv7TdZmipTv218Tk4yfh3bxmMUGqRgWiNsUAZ ESaLYWbWMa5ZTQV+fWE/fE/inl1USXeGAV2QPYd6mUsynb6LuguUeUrNE/1z7wPI mNdvv+/R4H5sWPsRWpr6sibzrHPJvc/2xXbn4cieitKrASCIfgyhjh+OjTvJ6o0A KAPyzhLUGi0/pBXCL4o/A5AzGlnxc0Kkn+iN9JVq1pV43ovRM/BAI5UDOZmgsSDO qVGbUkcmn8A4AjKfidFbC5qOUtc5E09L8hHbuXtFq/3uPy+/8NSbzAgCmtfH5Lr+ 2ldHyvc8gKi+fpd15VMeoAsCOL1xuQIHmpa418YFPZpO2x2IykHF93mwsTz6cVZ7 xgpnfkYErs+QxAfz =8TVh -----END PGP MESSAGE-----
Using the RSA public and private key generator.
Alice will then send the encrypted message to Bob. If it is intercepted, it won’t be readable.
When Bob receives the message, he unscrambles the message with the public key Alice sent him earlier. Bob can trust that the message came from Alice because Alice’s public key unscrambles the message.
… which gets us back to how private and public keys are used in Bitcoin transactions…
Private and Public Keys in Bitcoin Transactions
So how are private and public keys used in Bitcoin transactions? Answer: They are used to establish trust.
Trust
Each transaction has
- inputs
- outputs
- a signature
Inputs
The inputs are the outputs from previous transactions. The sum of these inputs should add up to the outputs.
Outputs
The receiver must provide a Bitcoin address to the sender. The sender’s public key is converted with a hashing function into a Bitcoin address. The hashing function shortens the public key and obscures it to help prevent hacks until the full public key is revealed.
A Signature
To prove that the inputs of the transaction belong to the sender, the public key that created the Bitcoin address is revealed. This public key is passed through the hashing function to confirm the hashed result matches the Bitcoin address.
The private key is used to create a signature. The same public key that is revealed above can be used to decode the signature. If the public key decodes the signature it proves that the private key was used to encode the signature. Notice that the private key never has to be revealed so it stays secret the entire time.
This is similar to the wax seal establishing trust as described above.
Using A Computer to Verify
As we discussed above, a Bitcoin Node verifies the sender has a legitimate Bitcoin balance to send in a transaction by
- Verifying the Bitcoin address used by the inputs to the transaction match the public key.
- Verifying the public key can decode the signature – which means the sender owns the private key as well.
Bitcoin Transaction Example
 At the beginning of this transaction, assume Alice has 2 Bitcoin and Bob has no Bitcoin.
At the beginning of this transaction, assume Alice has 2 Bitcoin and Bob has no Bitcoin.
To start, Bob needs to tell Alice where to send the Bitcoin. He will normally generate a receive address from his Bitcoin wallet. The receive address is a special form of a generated public key.
Alice will look through her Bitcoin wallet until she finds a large enough amount of Bitcoin. She can either pick a larger amount or can use many smaller amounts that add up to the amount that Bob is asking for.
Then Alice creates the transaction with her Bitcoin wallet. This happens automatically but what is happening is that she is gathering the paper money that is more than what Bob needs, specifying who the receiver is (Bob with a Bitcoin Address of 35FUAFsAAR5jcQ9MtTTDqqyDbwjRMHttKR ) and signing the transaction with her private key as proof that she owns the inputs (previous transactions from Charlie).
 Alice now sends the transaction to the Bitcoin ecosystem.
Alice now sends the transaction to the Bitcoin ecosystem.
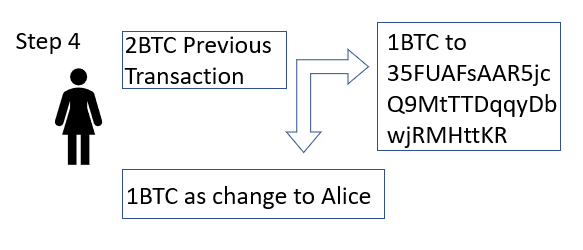 Bob now has 1 Bitcoin and Alice has 1 Bitcoin. It is a little more complicated than this because she’ll need to pay a small transaction fee so Alice’s change may only be 0.9995 Bitcoin.
Bob now has 1 Bitcoin and Alice has 1 Bitcoin. It is a little more complicated than this because she’ll need to pay a small transaction fee so Alice’s change may only be 0.9995 Bitcoin.
Conclusion
That is an overview of how Bitcoin Transactions Work. Visit our other posts to learn about other aspects of Bitcoin.